Millions of devices are spread throughout the globe, connecting people to the web. Thanks to these devices, we can enjoy the web as we want to. We can surf as long as and whenever we want. Thanks to these devices, our life just gets easier. Pretty amazing, isn’t it? How those small devices can do so many things in our life. The question is, are those the only things those devices do to us? What I mean is, are those devices even safe at all? What about potential security risk? Are those devices 100% hacking free? With those devices, can we still stay safe online?
Before we can connect to the web, there are some steps we need to complete. Some of them require devices like modem and router. Without these devices, browsing the web is impossible. We rely on these devices to bring the web to us. They are our portal to the web. Now, what if I told you that millions of these devices are vulnerable to malicious attacks? What if I told you that hackers can get through these devices? Can you imagine things they can do to you? And that’s not all. Your VoIP phones and IP cameras also share the same backdoor.
What do you think about these devices now?
Hacking Never Gets Easier
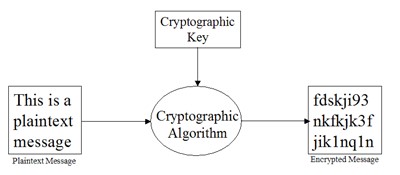
In the past, when someone wanted to hack your devices, they need to do it one by one. But today, thanks to our manufacturers, they can cut their hacking time. Most devices we use to connect to the internet today share the same HTTP Secure (HTTPS) certificate or Secure Shell (SSH) cryptographic keys.
Now, does it change anything in how we connect to the internet?
Particularly not. You can still connect to the web without any problem. In fact, you can’t even tell the difference. However, if we look further, we may find something interesting. As you can see, applying the same HTTPS or SSH key might help companies in cutting their production time. It helps them to make more products. Therefore, they can make more profits. However, doing that thing also mean one thing. They invite cyber criminals to do one thing they love the most: hacking.
Let’s imagine you just purchased a house. This house has 2 floors and 4 doors at each floor. Each door has its own key. A good developer will give you different keys for every door. Without the right key, no one can enter a particular room. For example, a key to your working room unlocks only your working room. The key to your garage can’t unlock your warehouse and so on. This is how our ideal house look like, at least from the security aspect.
However, there is a bad developer who only thinks about making money. This developer came to you and gave you the keys. There are 8 keys for your 8 doors. You were not really interested in checking the keys, so you left them. A week later, accidentally a stranger found one of your key. From what the developer told you, that key should unlock “only” your garage. You realized the key is missing, but do nothing because you left nothing precious in your garage. What you don’t realize is that person realized he can use the key to unlock all of your doors. So, in the silent night, he comes to your house and steal everything.
This is what actually happening now. Your devices might just share the same key as other millions of devices out there. With this, hacking never gets easier than ever.
One Critical Mistake that Sacrifices Your Security
SEC Consult found this problem in its recent survey of IoT devices. This hacking survey involved 4,000 embedded devices. Manufactured by 70 vendors, they found something interesting about these devices.
- At least 4 million devices were sharing at least the same 230 crypto keys.
- More than 3 million devices were sharing more than 120 HTTPS certificates
- More than 900,000 devices were sharing the same 80 SSH host keys
- X.509 HTTPS certificates
- SSH hot keys
Is Your Device Vulnerable to this Hacking?
- ADB
- Actiontec
- AMX
- Adtran
- Alpha Networks
- Alcatel-Lucent
- Aruba Networks
- Bewan
- Aztech
- Busch-Jaeger
- Cisco
- CTC Union
- Clear
- D-Link
- Comtrend
- Deutsche Telekom
- Edimax
- DrayTek
- General Electric
- Huawei
- Green Packet
- Innatech
- Infomark
- Motorola
- Linksys
- NETGEAR
- Moxa
- NetComm Wireless
- Observa Telecom
- ONT
- Opengear
- Philips
- Pace
- Robustel
- Pirelli
- Seagate
- Sagemcom
- Seowon Intech
- Smart RG
- Sierra Wireless
- TP-LINK
- Technicolor
- TRENDnet
- Totolink
- Unify
- Tenda
- UPVEL
- Ubiquiti Networks
- Ubee Interactive
- Western Digital
- Vodafone
- ZTE
- ZvXEL
- Zhone
- United States
- Brazil
- Mexico
- Colombia
- Spain
- China
- Canada
- Taiwan
- Russian Federation
- United Kingdom
Is There A Way to Stay Safe from This Hacking?
The threat is imminent.
The damage is unimaginable.
However, there is still a way to stay safe online. Read our article on how to stay safe with VPN Asia.
 English
English
 German
German Dutch
Dutch Thai
Thai Chinese
Chinese