Most of us spend too much of our time looking for the best software, such as VPN, to ensure our online security. We forget that internet connection requires both software and hardware, such as routers. As we put less concern in protecting our devices, we leave our security door opened to the net marauders. These people have been making our devices as the perfect target of their attack.
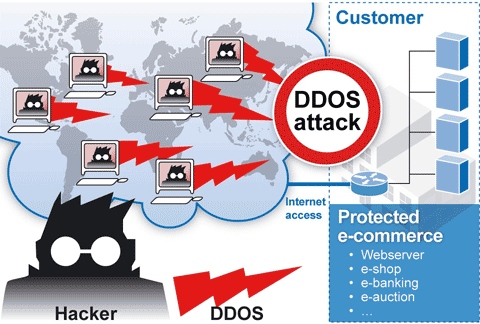
Security companies from Asia, Europe, and America reported that within the last few years, there have been a rapid increase in malware attack, particularly targeting home routers. However, this attack is not the only security threat we have. The reasons may be still unclear, but not all routers are safe. Most vendors do not equip their vendors with advanced security components and, in fact, update the device once you installed them, including giving the security updates. So, if I were a hacker, I would first target your router as you leave your security door opened for me.
Cross-site Request Forgery and VPN
Most vendors protect their routers by applying strict rules on how users may alter the router settings. Typically, accessing and changing the settings require your presence on router local network. However, it appears that this is not the only way to alter the settings, even if you have secured your connection with extra stuff, such as VPN.
Some users in Asia reported that some home routers come with a security backdoor. These backdoors are initially aimed by vendors to provide an easy access to service the routers whenever necessary and the vendors are supposed to be the only one who knows these backdoors. Unfortunately, they do not as net miscreants have also discovered these doors to create massive denial-of-service (DOS) attacks.
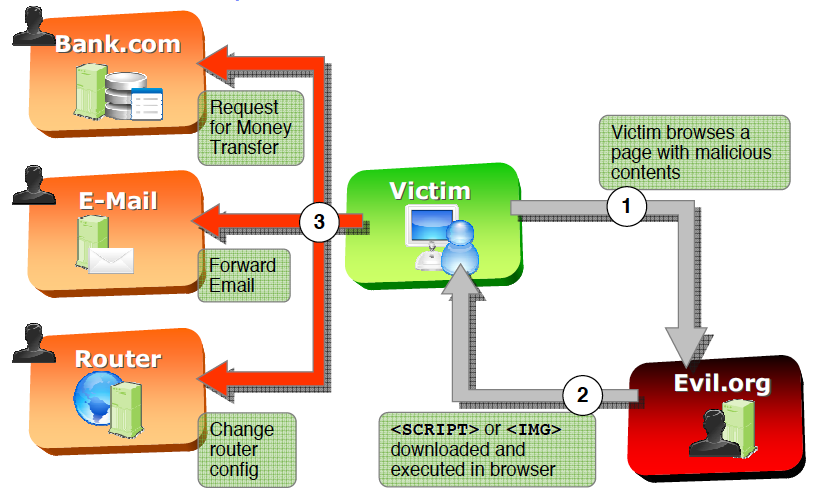
Even if a backdoor does not exist in your router, hackers can still compromise it by doing ‘cross-site request forgery.’ First, they redirect you to a malicious website. Without a secure connection, like VPN, this site would use your browser to ping to your home router. With some pretty codes, your router would think it was you sending the request from local network, not the malicious website. Once the hacker opened or created a channel between your router and browser, there would be lots of option for the hacker to make your day worse than you can ever imagine, from changing your DNS server, opening a security hole in your firewall, changing your administrator password, and many things else. All the hacker needs to do is redirect you to send the requests.
The best countermeasure is keeping your email address safe and check your device security. Do not easily give your email address to someone or a website you cannot trust, even if it appear similar to the website you trust and use VPN to secure your connection. You should also contact your router vendor to check whether the device comes with a backdoor or not. If it exists, make sure the vendor always give the security patch.
 English
English
 German
German Dutch
Dutch Thai
Thai Chinese
Chinese