There are some similarities between virus and malware program. In specific meaning, malware program enters your system and utilizes the various resources in it for its own interests. This exposes your system to various risks with undoubtedly strong consequences. That’s how these malicious attacks get their name. It is also, in most cases, how attackers took inspiration of their attacks. The recent, MERS attack for example, had inspired attackers around the world to mimic the attack pattern.
The latest Middle East Respiratory Syndrome (MERS) outbreak in South Korea had ‘inspired’ many email attackers. The outbreak itself took 36 lives, with more than 186 infected people. So, how do the attackers take benefit of this attack? These email attackers scared their victims with wrong information about MERS outbreak. They took benefit of people’s panic. By using link attached in their email, these people tricked their victims to download malware programs into their PC.
Malware is Worse with Our Fear
Early this month, Symantec discovered a malicious email campaign. The mail advocated its recipients to download an attachment Microsoft Word format. The file itself, as the attackers claimed, contains a list of the patients and hospitals that had been infected by the MERS virus. Of course, that list never exists. The attached file was actually an executable file (.exe) that Symantec revealed to be a Trojan.Swort. The malware itself contains low level of threat. It’s only know infection method is through manual download.
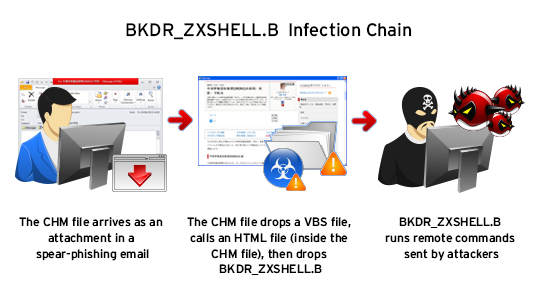
This month, Trend Micro, a firm that deals in cloud security, reported a similar case in Japan. The attacker sent an email to a local media company. As the attacker claims, the email contains a medical-backed information on how MERS could be prevented. However, upon opening the email, something weird happened. It redirected the recipient to a malicious site, which ZXShell exploit kit.
ZXShell itself is quite popular among email attackers. Security experts believe this attack was connected to the 2014 Sony hack. It is not just a coincidence that both attacks involve with attacking media companies. The patterns were similar as well as the expected result. In the historic Sony attack, the malware leaked confidential information, including personal emails. Other leaked information include company decisions, some of which were of a sensitive nature to the public domain.
Bearing this in mind, there is one important thing we should learn. Even if we are not connected somehow with MERS, at least we should know about it. This way, we can become aware of the situation and not easily tricked with false information. The attackers only require a click to plant the malware in your system. They use our paranoia and fear to exploit us and our personal data. Therefore, we recommend you not to opening attachment(s) and/or link(s) you aren’t certain. In most cases, this tip greatly reduce the risk of malware attack.
 English
English
 German
German Dutch
Dutch Thai
Thai Chinese
Chinese