Hacking, a never-ending topic. Don’t get surprised if someone hacked you today. It’s no longer weird when you got this. Hackers are everywhere and they don’t mind to attack you or anyone. They are always looking for vulnerable victims. The one they can use for their own purposes.
Those hackers are relentless. They won’t stop until they got what they want. Before that happens, you must stop them. Now, let’s just assume that you realized the hacking attempt. The question is, what should you do know? What is the next step? Is it possible to stop the hacking? Is it possible to keep your system and everything in it, safe?
Let’s calm down for now. Take your breathe. Those hackers may be dangerous, but that never means they are invincible. You can stop them. 
Your Simple Guide to Stop Hacking
Begin the inspection
Most people link hacking to data breach. Some parts of it are true. However, not all data breach indicates hacking activity. There might be something else that causes it. Therefore, don’t panic if you lose some files. Perhaps you just forget about where you put them. Perhaps, you forget that you deleted them. There are so many other explanations besides hacking. So, calm down first. Then, ask yourself some questions. Is there something you forget? Have you checked all the security measures? Have you checked your emails? Try to narrow down the possibilities. If hacking is your only suspect, let’s move to the next step.
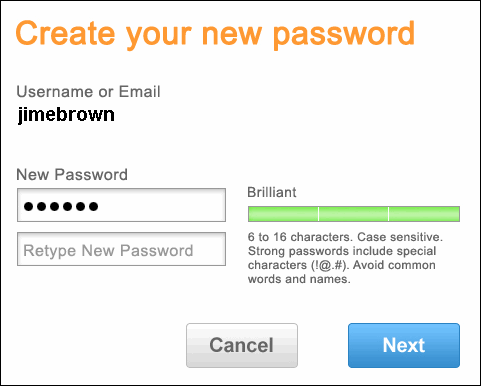
Reset all your passwords
A hacker’s first job is to get your password. They can’t do the rest without it. Your password is the key to everything. So, if you’re certain that you’re being a hacking victim, please do reset your password. Avoid using general passwords. Avoid using your name or something close to you. At least, your password must contain 1 unique character, letter, number, and uppercase letter. Try to make it as long and complex as possible. This will force the hacker to spend more time guessing your password. Meanwhile, you can protect your system even more.
Check all your accounts
Some hackers are ‘generous’ enough to get into your system. But, do caution, some others are not. They attack you to get your personal information. Your financial information, for example, is one of their favorites. Once in, they can grab your credit and debit card number, banking account number, credit report, home address, phone number, online banking, and many more. They will leave nothing for you.
Some hackers even ask you for ransom. Even after they stole everything, they will ask you for ransom. Therefore, before this happens, make sure you have secured everything. Check all your financial information for suspicious activities. You can contact your bank for help. If you found anything suspicious, report it. Block your card, if necessary. This will prevent the hacker in using your card. Meanwhile, you can ask the bank to track who did the hacking.
Don’t forget your connected accounts
Many people often easiness today. We demand everything to become easier than ever. Here is one thing we don’t understand. While things may go easier as we want, they also become more vulnerable. Let me show you an example. How often do you fill an online registration form to create a new account? Today, less people choose this step. Instead, we sign up using our existing e-mail address. Will this ease everything? Not really. It may, in fact, fasten the registration process. But, do you know that by using existing accounts, you give the app your personal information?
Here is the another thing we don’t realize. Connected apps make hacking easier. Hackers only need to hack one of your email. Once done, they can break into all apps you use. They can grab everything they like. All thanks to your connected apps.
Now, tell me. What do you think you should do now?
De-authorize all connected apps
If you know what I mean back then, do this now. De-authorize all your connected apps. That hacking will only go worse if you keep your connected apps.
Don’t worry. Once we cleared the threat, you can re-authorize it later.
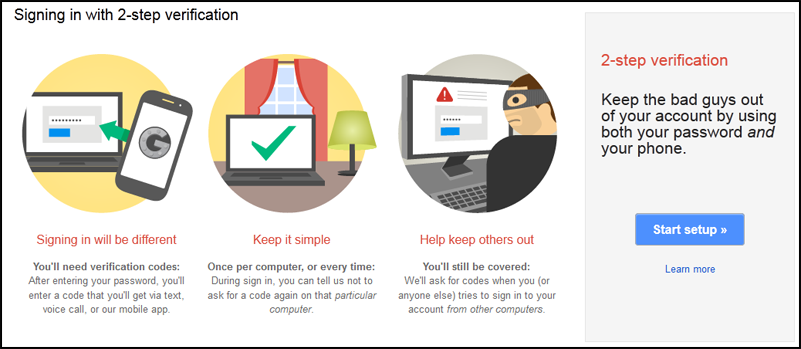
You need two-factor verification
A complex password is what you need. But, what if there is a way to improve it? But if I told you, you can make it more complex? That way exist. You can make it. If only you don’t mind to follow these steps 🙂
This two-factor verification will create another security layer to your account. Anyone who wishes to enter it must get through this layer. Without it, no one can enter it. (PS: not even you, if you forget the key)
Account recovery
We hate the worst. However, we must expect it. We must learn how to deal with the worst. In hacking, you should expect this worst thing. You should expect losing control of your account. Lucky for you, there is always a way to recover it. Most major services today can help you with this. Log into your account. Then find the account recovery options. You will have your account back in no time.
Don’t miss the update
There is no perfect system. Not even the best is free from vulnerabilities. You can name any system, device, or anything you want. None of them is perfect. But, that doesn’t matter. The only thing matters is how we learn. All providers learn about their mistakes. We learn about our vulnerabilities and fix them. That’s why there are updates and patches. Your device manufacturer provides them to fix all vulnerabilities inside your system.
To get your updates, go to your System Settings. Find the Update option. If possible, set your system to check and install the updates automatically. This way, even if you forget, your system won’t.
I suggest regularly updating your system. Those patches will fix any known vulnerability. Don’t ever lose any. This is the mistake hackers want you to do. Any slight mistake will make their hacking easier.
Scan your device
Over confidence is sometimes dangerous. This rule applies in hacking. Some victims are too confident that they’ve cleared malicious apps from their system. They are too confident to say they are 100% safe. Here is the fact. Some malicious apps are well hidden beyond your reach. Some are even untraceable. So, how do you remove them? Well, there is another rule. There is always a better way to do anything. There are worthy security solutions out there. Use them. These tools will help you scan your system for any malicious script. Not even the well-hidden one can escape. Don’t know which one to pick? Why don’t you google it?
Also, don’t forget the update. Your tool maybe at the top of the list, but it won’t help if you miss the updates. So, keep your eyes on 🙂
Use VPN
A great power that lies in a simple app. A VPN can help you kick hackers away from your system. Advanced encryption protocol secures your transmission so no one can see it. Anonymous browsing allows you to be invisible on the web. All this feature will reduce the risk of hacking. Combine this with all you’ve learned here and I guarantee you, you will be much safer than you can imagine.
Spread the awareness
You’ve done so much to stop the hacking. You have secured your system. You have even created a wall for those hackers. So, does this mean the end?
I would like to answer yes for that. Unfortunately, I can’t. Hackers are relentless, I told you that. There are so many ways for them to attack you. If they failed on you, they will find another way. Your close relatives, perhaps. What if they hacked them and find some interesting information about you? This will help them to once again hack you.
Here is my point. All of us are connected. You can’t stay safe from hacking if others don’t. So, stay safe. Spread the hacking awareness. This is the best way to stay safe online. Tell everyone what you’ve learn. Grow the awareness in them so everyone can be safe again.
 English
English
 German
German Dutch
Dutch Thai
Thai Chinese
Chinese