The most dangerous malware is not the one with most destructive ability. It’s the one that exists on your system, yet no one can find. This type of malware has been targeting finance industry for years. Payment card processors, banks, ATMs, and other financial services have been suffering from their attacks. Now, with Nemesis malware, the attack will only go worse.
Nemesis is born for one thing. To pluck all sensitive card data out of your PC. But before that, it needs one thing. It needs to somehow make itself invisible. How? By hijacking your boot sequence. It will force your PC to run a highly-intrusive code. As the result, your PC adds Nemesis code into it’s boot sequence. What you’ll see next is your PC runs this malware before your OS. That’s how you won’t find this malware as easy as other malware. It has already gone deeper into your system. Far beyond your OS.
The Threats Behind Nemesis Attack
It was earlier this year when security experts found this so-called bootkit. It is part of the bigger problem, “Nemesis.” It is practically a package of malware. Everything you dream the worst about malware, is in there. So, what are inside this suite?
- Programs to transfer your files
- Injecting processes
- Keystroke recorder
- Screenshot captor
- Other carriers of malicious actions
From what security experts told us, we need a different way solve this problem. Nemesis won’t be so easily eradicated, unless we fight it from its source. We need something that can search and access raw disks at scale. We need this tool to search for any evidence of Nemesis. Without it, nothing we can do.
By any means, Nemesis possesses serious threat. The real problem here is, it’s not the first of it’s kind. Then, should we have already had the ‘patch?’ If this attack type was identified before, shouldn’t we have a solution to fix it?
To gain stealth and persistence, that’s what Nemesis born to do. But, Nemesis is not alone. For 5 years straight, another malware, TDL, has done similar thing. Also known as Alureon, this rootkit not only attacks Window, but also Mac. Unfortunately, Apple denied to believe it. That’s when a security expert tried to exploit the weakness inside Mac. He deployed a proof-of-concept attack to a Mac unit. What happened then cleared Apple’s mind. The attack successfully replaced the original firmware. The attack was never meant to exploit any sensitive data. No one was affected then. But, it’s more than enough for Apple to realize the weakness. Later, they released security patch for the weakness. Still, we have a big problem right before us. TLD and Nemesis are just the beginning. What it shows is the future. Malware is evolving. Today they can hide on our PC. Who knows what they can do in the future? If this is the beginning, what things should financial institutions hope in the future?
Why Nemesis Targets Your PC Volume Boot Record?
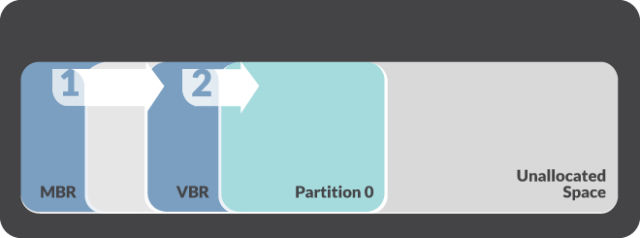
First, what is a volume boot record?
A volume boot record is simply a small piece of code. But, it’s not just an ordinary code. This code tells your OS to initiate boot process. Due to its function, you can only find the code inside an individual partition. To be precise, in the first sector of the partition. The process itself is similar to the following image:
When Nemesis attacks, it hijacked the normal sequence. First, it learns your system. During this process, all statistics will be gathered. That includes your OS architecture and version. Nemesis, itself, is powerful enough to deploy 64-bit and 32-bit attack. However, the decision will depend on your processor architecture. Only after then, the bootkit installation process will begin. All hard disks with MBR partition will be hijacked. Only hard drives with GUID Partition Table architecture will be spared.
A “BOOTRASH” installer is used for this. Once deployed, this installer will invoke a multi-step process. While it may not look dangerous, the real threat lies behind the visible process. This multi-step process secretly involves creating a virtual file system. This is where our real threats ‘live.’ Inside this system, the true malicious components reside. They live in unallocated space between your partitions. For the installation process to complete, Nemesis requires 2 things. First, your system should not be running a copy of BOOTRASH installer. Second, your system should have Microsoft .NET 3.5 framework installed. If your system doesn’t meet either one of this condition, Nemesis will quit.
The researchers also revealed other facts. The installation process also involves with the interception of some system interrupts. One of them is your BIOS interrupt. This BIOS interrupt is responsible for two things. First, miscellaneous system services on your PC. Two, patching related Interrupt Vector Table entry. Once the bootkit took control over your BIOS interrupt, it will be able to intercept memory queries. However, it will only possible after the OS loader takes control. Then, the original VBR will receive the control passed by the bootkit. This process will continue the boot process. While your PC is loading the OS, the bootkit will be doing it’s job. It will intercept the interrupt. Then, it will scan your OS loader memory. During this process, specific instruction will be gathered. This instruction transfers your CPU to protected mode from real mode. Taking this instruction is important. Nemesis requires to patch your Interrupt Descriptor Table. It should be done every time your CPU changes into protected mode from real mode. A modified interrupt handler is involved in this patch. This handler redirects control to Nemesis bootkit. This is done every time the process executes an address. Without this, Nemesis bootkit won’t be able to intercept and detect particular points of your OS loader execution. That also means, it won’t be able to inject Nemesis components.
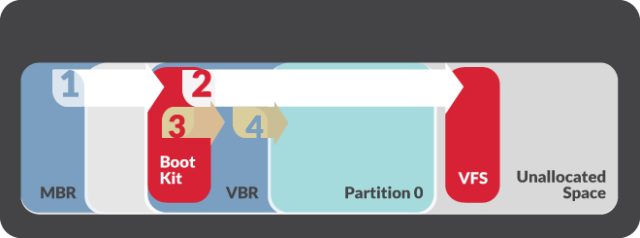
There are two possible places where Nemesis code lives. It is either in your Windows registry or virtual file system. At these places, your conventional antivirus won’t find Nemesis. The good news is, Nemesis can’t hide everywhere. There is one place you can find it easily. Ever heard about your live memory? It’s the only place where you can find Nemesis. So, better make this place as your priority. Another important thing to remember is how this malware works. As I’ve told you before, the malware will load and execute at every boot. You can’t run from it unless you do the tricks. You should remove the virtual file and bootkit components. Without these, even if you reinstall your OS, the malware will always be there. Not even wiping your OS partition will work.
Once Nemesis hijacked your boot, there’s only one way left. You must wipe your OS. Then, reload it. This step will cure your PC.
Also, please remember to use GUID partitions on your hard drive. As part of the Extensible Firmware Interface initiative, GUID partitions are much safer than MBR. If you want to keep Nemesis away, start with protecting your hard drive. GUID partition is a good way to start. Then, you can think about applying advanced protection. Something like using VPN Asia for your company..
 English
English
 German
German Dutch
Dutch Thai
Thai Chinese
Chinese